Where is ERC4626 Headed in 2023
The little standard that could.
✨ TLDR; If you just want to see the map, please scroll down!
Many crypto Founders I speak to are committed to the space but looking to make a strategic pivot.
One one hand, several markets in crypto have not matured at the rate we expected.
On the other, new research themes are emerging, promising to create new markets with them.
We've covered many of them here: intents, hooks, ERC6551, UniswapX, proof-of-personhood, arcade wallets, coprocessors.
Founders win by nailing market timing.
Timing is all about using recently available technologies to build emerging technologies all while addressing a fundamental user need.
But how can we find opportunities that are well timed and meet user needs?
Wardley Mapping
One tool in the arsenal is Wardley Mapping invented by its namesake Simon Wardley.
It's an elegant way to zoom in on a specific part of the value chain and studying how different components are assembled to solve for user needs and their respective maturity levels.
Simple Wardley maps look like this:
Each node is a technology in a different stage of development. A special node exists to signify the “customer”
Nodes are positioned on a two-dimensional grid with two-axes: the higher a node is on the y-axis, the more visible in the value chain it is to users; the further the node is on the x-axis, the more developed it is in the market
Genesis means that the concept is just an idea at R&D stages, Custom Built represents bespoke solutions, Product stands for technologies that are sold as products and Commodity is the final stage where the product becomes heavily commoditized (e.g., compare buying a computer vs. buying cloud compute)
Similarly “Visible” and “User-facing” components in the value chain are more visible to users – either directly purchased or represent user needs. Invisible components usually are used or purchased deeper in the value chain but not visible to users directly (apart from the most discerning users) and are further divorced from user needs
Finally, two nodes are connected if one uses the other in the value chain.
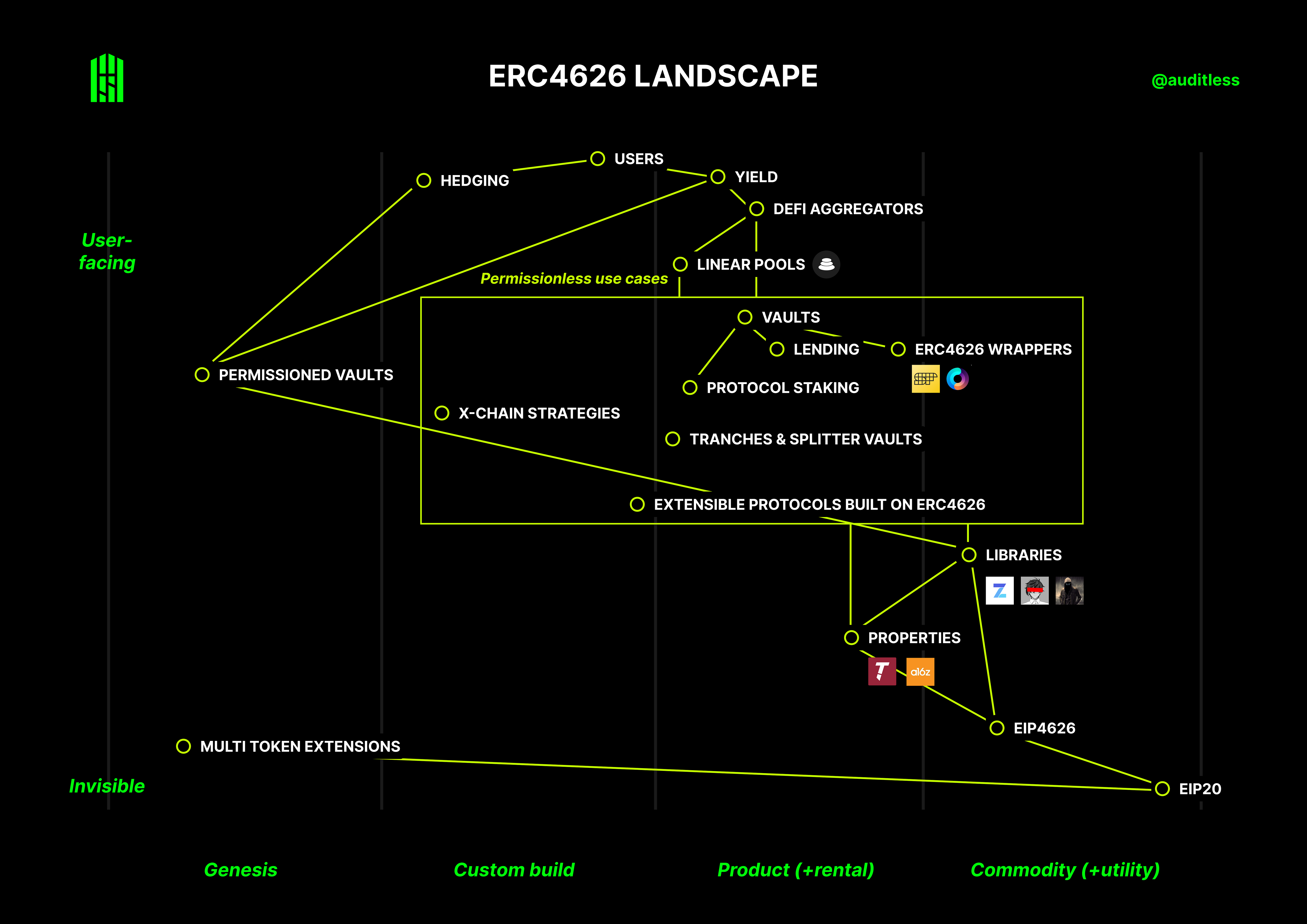
An overview of ERC4626
I thought a good place to start would be to apply this model to study the ERC4626 yield-bearing vault standard and its ecosystem.
I'm a big fan of the standard and the Alliance built around it.
I used ERC4626 in several projects, gave a talk on its security properties and created the Cairo template.
So this was really fun.
Legend
DeFi Aggregators. These super apps can now support many yield sources with a single interface.
EIP20. The ERC20 token standard. Note I've used “EIP20” instead of “ERC20” to differentiate between the spec and the token standard implementation itself. If using ERC20, I would have had to place the node much higher as ERC20 tokens are well understood and widely used.
EIP4626. The ERC4626 token standard itself as described here: . See EIP20 above.
ERC4626 Wrappers. Standard wrappers are being developed for lending and other yield sources that currently don't support ERC4626 out of the box.
Extensible Protocols built on ERC4626. Several teams now use ERC4626 as an interface for extensibility. PoolTogether accepts ERC4626 vaults to create new pools and Uniswap V4 hooks are being envisioned that can support general yield sources.
Lending. Lending protocols are one of the first to natively adopt ERC4626 as an interface for supply.
Libraries. Standard templates for implementing ERC4626 vaults. Popular ones include OpenZeppelin, Solmate, Snekmate.
Linear Pools. Linear pools create a pair X/Y where X is the underlying asset of an ERC4626 and Y is the ERC4626 vault share. These pools can be used to trade shares without having to take mint/redeem actions.
Multi Token Extensions. ERC4626 supports one underlying token per vault. Multi Token Extensions such as the Superform MultiVault extend that to multiple underlying assets.
Permissioned Vaults. The ERC4626 interface provides a convenient generalization for treasury management solutions, hedge funds and other entities that are looking to generate yield onchain with capacity-constrained strategies.
Properties. Security properties can be used to test standards compliance of any ERC4626 vault. Two popular options were developed by a16z and Trail of Bits.
Protocol Staking. ERC4626 is becoming a natural interface for single token protocol staking with Maker's sDAI being the canonical example.
Tranches & Splitter Vaults. The limitation of single underlying asset can be overcome by having one ERC4626 vault represent a single tranche in an underlying structured product.
Vaults. ERC4626 is becoming the canonical interface for yield aggregators and other strategy vaults.
X-chain Strategies: Some protocols are experimenting with allowing users to make deposits that will then be used to access cross-chain yield.
Let me know what you think and reply with any feedback.
Thanks to:
Blake from Superform
For their feedback and suggestions.




Excellent